At present, cyberattacks cause a lot of havoc in many countries. Ransomware is one of the categories of malware attacks that is increasing rapidly. In this context, STOP/DJVU ransomware continues to get more sophisticated. This threat can corrupt your JPEG images and render them completely unusable.
If you find that your JPEG images are not accessible, then it is a possibility that your files are affected by this ransomware. Remember that you are not the only victim of this issue. You should need a few in-depth understanding to get the significant answers to repair corrupted JPEG files.
In this article, we explain the STOP/DJVU ransomware along with how it can infect your computer. Additionally, you will explore the effective ways to repair the affected JPEG files.
Introduction to STOP/DJVU Ransomware
STOP/DJVU Ransomware is a form of malware that first got attention in 2018. This ransomware encrypts the files on your system and then demands a ransom to decrypt them. This file-encrypting virus is typically downloaded from software crack packages, keygens, and other malicious applications available on torrents and other similar sites.
It secretly intrudes on your system and encrypts your files to make them inaccessible to you. After that, it drops a note informing the encryption and asks you for the ransom money to decrypt your files. It is a trojan malware that quickly spreads encryption in the background to infect your system. Mostly it targets the popular file formats such as .doc, .pdf, .jpg, .jpeg, .mp4, etc.
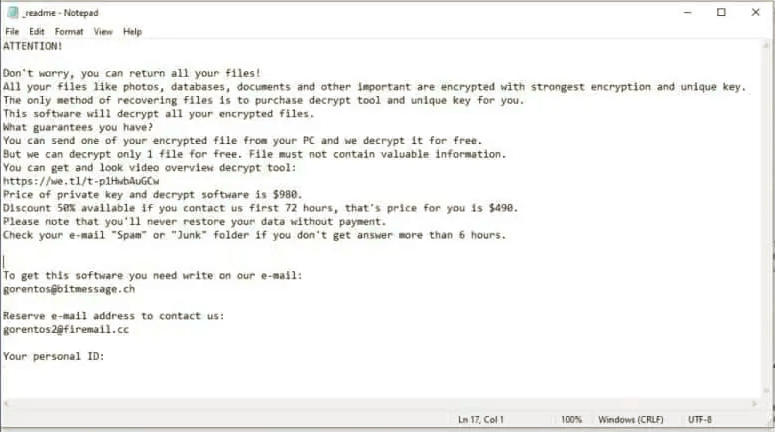
STOP/DJVU Ransomware only encrypts about 5MB of the files. Once it succeeds in adding the encryption, it updates the affected file with a .djvu extension. Further, you will receive a readme.txt that contains a ransom note, including the details about the mode of payment. In addition, the money gets doubled if you fail to pay within 72 hours.
After understanding the STOP/DJVU Ransomware, let’s go through the different ways that enable it to access your system.
How does this DJVU Ransomware Intrude your System?
In this section, we are going to understand the different ways through which STOP/DJVU Ransomware could have gained access to your system.
#1 Through Freeware Programs
Probably this virus may intrude on your computer through the freeware programs. Torrent and many other similar sites are the sources of these programs. Therefore, it is recommended to inspect the sites before downloading or installing a freeware program. Otherwise, the malware gets access to your system and corrupts your crucial data.
#2 Installing Fake .exe
Usually, there are many reasons that arise when you need to download extensions. However, you have to be extra careful while installing them. Otherwise, there will be a chance of such ransomware getting access to your computer through some bogus extensions. Some fake extensions deliver the threat and install malware on your system. Once the malware gets installed, the extension deletes itself. Therefore, it is essential to watch out for the extensions you download.
#3 Via Malicious Scripts
Many viruses belong to the Trojan family that delivers such ransomware. They have the potential to gain access to your system via malicious scripts. The suspicious sites bring such scripts as you click on the popups or banners on these platforms. It could then frequently redirect you to the site that delivers the ransomware on your computer.
#4 Visiting the Unsafe Networks
Another prominent source of STOP/DJVU ransomware is adult sites. Some of the sites are banned in a particular country. However, we gained access to them using free VPNs available online. When you visit these sites through an unsafe network, it renders the malware to your system that results in such ransomware. Therefore, it’s advisable not to breach the limitations of using such networks.
Significant Ways to Decrypt JPEG Images Affected by STOP/DJVU Ransomware
Since you know how STOP/DJVU ransomware works and the potential ways through which it gains access to your system. Let’s discuss the practical solutions to repair the affected JPEG files.
Step-1 Separate the Infected Device
Some infections may intrude your system through external storage. Therefore, you need to isolate the device to prevent spreading these infections throughout the local network. You can perform the following steps to disconnect your device.
Disconnect your Device from the Internet
The initial step is to isolate the device from any internet connection as soon as you discover the infection. If you are connected with Ethernet, disconnect it from the motherboard immediately. Follow the steps below to isolate your device from the internet connection.
- Open the Control Panel and click on the Network and Sharing Center.

- Now, select the Change Adapter Settings to view the Network connections.
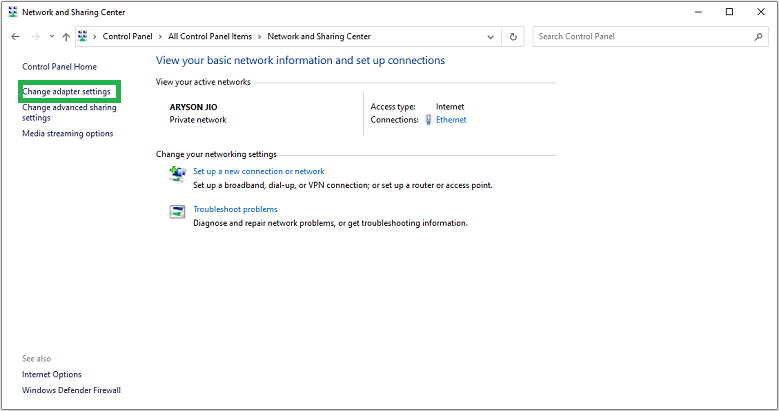
- In the end, select each connection and click Disable to isolate your device from the internet.
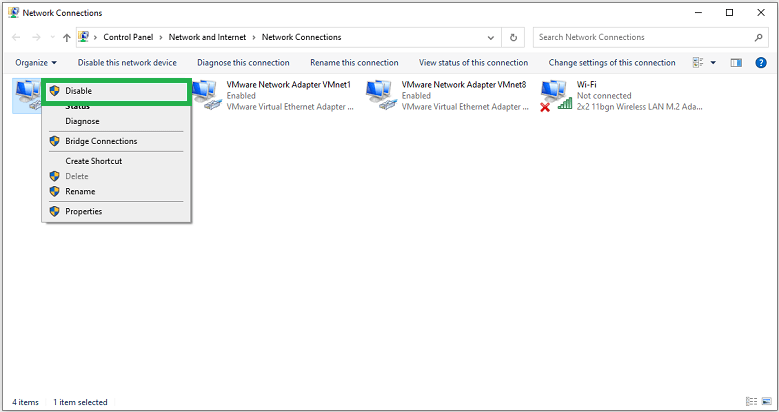
Remove/Unplug the External Storage Device
If you are connected to any external storage, then immediately unplug it. This STOP/DJVU Ransomware has the potential to infiltrate your storage devices. It is essential to limit the scope to decrypt the JPEG images affected by this ransomware.
Sign Out from the Cloud Storage
It is essential to log out from the cloud storage because it has the potential to hijack your cloud storage. Therefore, it is required to temporarily uninstall your cloud storage software till you decrypt the affected JPEG images.
Step-2 Analyze the Online or Offline Encryption
To get rid of STOP/DJVU Ransomware, you need to identify if the encryption was using an online or offline key. Some of these infections introduce themselves by sending messages about the encrypted files. You can analyze the encryption by following the below steps:
- Find the SystemID.txt and PersonalID.txt files in your system. These files contain the encryption IDs used to create STOP/DJVU Ransomware.
- Also, you can refer to the _readme.txt file to identify the personal ID.
- You can find the offline keys that end with a “t1”. After that, it will be easier to retrieve data from the affected JPEG files.
Step-3 Use STOP/DJVU Decryptor to Repair the Encrypted JPEG files
After identifying the Personal IDs and offline key, you can use any free Decryption software such as Emsisoft STOP/DJVU Decryptor. You need to perform the following steps to repair JPEG files infected by STOP/DJVU Ransomware.
- Download and Install Emsisoft Decryptor.
- After opening it, click Yes in the User Account Control window.
- Then, you need to Agree to License Terms to run the software.
- Now, click on the Add Folder option to select a location from your system. By default, it is set to C:\ partition.
- In the end, click on the Decrypt button to start the decryption process.
Now you can access the affected JPEG file data after successfully performing the above methods. However, to avoid such scenarios, you should keep the following suggestions in your mind.
Tips to Avoid STOP/DJVU Ransomware in Future
Although there are ways to repair the affected JPEG files, you still need to keep the following points in mind to avoid a similar instance in the future.
- Install a secure and reliable antivirus on your system and avoid using the cracked programs.
- Keep your Windows firewall active to prevent future threats.
- Ensure that your operating system and other programs are updated to the latest version.
- Always visit the official sites to install or update the programs on your system.
- Do not open the Spam emails and avoid downloading the pirated games, software, or extensions.
Final Verdict
The STOP/DJVU Ransomware infection can be harmful and restricts you from accessing the files in your system. We hope that now you understand this infection and how to decrypt the affected JPEG files. In the end, we provided some tips that will help you to avoid similar scenarios in the future. If you have any other queries regarding photo file repair, then try photo repair tool which makes accessible any kind of file from major photo file corruption.